eNom and Afternic: Conflict of Interest?
My first registrar was Bulk Register, now owned by eNom. (Actually, it was Network Solutions, but I don’t like to talk about that.) I still have a few accounts I didn’t switch over to my current registrar because they aren’t due yet, but an odd thing happened recently, confirming my decision.
I lost a domain.
Mind you, I’m used to regular notices as to what is expiring and when. My current registrar send out so many by every means imaginable that I’ve asked them to stop calling me. But without warning, a client called me up and asked why an unused domain usually parked on his active site went to a page trying to sell it.
I looked it up and found it was now owned by “BuyDomians.com“. No redemption period? Maybe a short one, but again, I wasn’t notified.
I contacted them and they offered it to me for several thousands of dollars. Based on traffic, all the free value estimators showed it worth $0 except one, which valued it in the three-figure range. I tried convincing them it was of no value to anyone but my client, but they insisted it was valued according to marketability and would not let it go to its rightful owner for much less.
Upon researching this type of situation, I found that an ICANN dispute costs a cool grand just to file and then it’s a crap shoot to interpret the regulations such that they are breaking the law. I believe they are, and simply can make it not worth anyone’s time to challenge them.
My old registrar insisted that I must be blocking their emails — which was ironic because we were communicating by email and my server team found no such record of receving emails from the address they use for notifications. They claim to send out at least three notices. (For another upcoming domain, I have to admit I later did receive one.)
But shortly after this fiasco — which ended in my offering free hosting for life for the client to make it up to them — I received an email from eNom with the following message:
Moniker and eNom are now live as Afternic DLS Premium partners
The reason this caught my attention is that when I tried to play nice with BuyDomains, I inquired about selling some of my own domain names. After all, if they’re charging an inflated price, they should be able to buy mine at a high price as well!
But they don’t buy domains. It’s handled by their sister company {drum roll please}, Afternic.
Maybe eNom is telling the truth about notifications. But they do have a huge potential benefit by letting them lapse. Just sayin’ …
Not Quite Slamming
It’s one thing when a company tries to sell you a service you’re already paying for to get you to switch. It’s quite another when they try selling you something you don’t even know you don’t have — or need.
I received these before. Using the same fear method as Domain Registry of America, they want you to pay them so that you don’t lose your Internet ranking. Who knows what service they are actually selling, but not paying them will not result in losing ranking — that is a lie. And they don’t specify what people do to make you findable.
This company, with all information hidden in the WHOIS for their name www.registerydom.com, is nothing but a page to receive your money. No contact information or link to ANYTHING. You basically pay and then have no way to reach them or know what you are getting. Real scumbags who need to be hunted down.
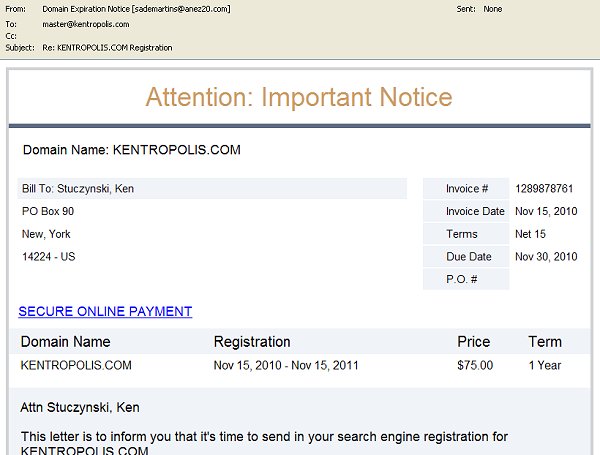
The funny thing is they have a disclaimer that “this is not an invoice” and get to the e-mail gives an invoice number! Here is the actual text, and a partial image:
This letter is to inform you that it’s time to send in your search engine registration for KENTROPOLIS.COM.
Failure to complete your search engine registration by Nov 30, 2010 may result in the cancellation of this offer (making it difficult for your customers to locate you using search engines on the web).
Your registration includes search engine submission for KENTROPOLIS.COM for 1 year. You are under no obligation to pay the amount stated above unless you accept this offer by Nov 30, 2010. This notice is not an invoice. It is a courtesy reminder to register KENTROPOLIS.COM for search engine listing so that your customers can locate you on the web.
This Offer for KENTROPOLIS.COM will expire on Nov 30, 2010. Act today!
The Boogeyman Virus
Some of us think that any problem, slowdown, or missing file on our computer is caused by a virus. And some of us remember fondly those years ago when a virus was the only thing you had to worry about. In reality most people have problems with the computer on a regular basis. Also, in reality, most of those problems are not viruses. But like the gremlins of aviators, we think of everything that can go wrong with our computer as being caused by a “virus”, when that is simply not true. But the question is, how do you know?
What are Viruses? Or are the Virii? Whatever.
A virus is considered the most primitive life form, because its sole function seems to be creating more exact replicas of itself. In fact, some scientists don’t even consider it a form of life, but a raw chemical machine, copying and recopying its genetic code to no other purpose or intention. And that is what a virus is — little more than code — which brings us to computer viruses. A computer virus is a program that is designed to make copies of itself on a machine or across a connection to other machines. It started out as a gaming geeks played to see how many computers that could infect around the world, sort of like a chain letter. They were mostly harmless, and did nothing more than take up a little space or memory resources. Some were nasty. They were designed to delete files or change settings to wreak havoc, but not before sending copies of itself to other computers.
Understanding how they do this is vital to protecting yourself. Remember how I said that most problems aren’t viruses? Well, most problems get on your system the same way that viruses use to make their copies throughout the world. Just like a virus in your body, it can only get there through some kind of contact. This means loading a program, either from a disk or from the Internet via e-mail or visiting a webpage.and just like viruses attach themselves to cells. Most viruses attach themselves to a program, even one that otherwise might be harmless. That is why your e-mail system will block some e-mails with some attachments, such as spreadsheets or executables (files ending in.EXE). That is also why most or all courts will not allow you per to present evidence via disk unless you use your own laptop.
Harmful programs are usually not classified as viruses, but malware or spyware. Their purpose is not to spread, just to infect, and infection means causing your your computer to behave in a certain way. Malware might mean more pop-ups or other advertisements, even when you are no longer connected to the Internet. Spyware are programs that send your information out to other people, such as your web browsing history, or in worst case, key logging software that records your keystrokes to steal passwords. Ironically, some Malware is designed to give you a warning that a virus or other problems are on your system, prompting you to download their software to fix it, usually for a price. Some webpages give you all warning of the problem with your system, asking you to take some action to fix it, when such action will actually infect your system with their software. That is why you should never respond to a warning unless you know it is coming from software already on your system.
Some problems that are mistaken for viruses may not even be on your computer. For example, people may say that they received e-mails from your e-mail address. Sometimes you may even receive e-mail claiming to be from your own address. In the old days, this would be the sign of a virus using your e-mail program to send itself to everyone you know. However, today this is almost always what is called “spoofing”. This is the equivalent of someone sending a piece of snail mail with your return address, even though they do not live with you. Your system did not send it out. Usually, they randomly selected your e-mail address from a spam list, and used yours instead of theirs. Unfortunately there is nothing you can do about that, except be aware that it can happen, and if it happens often, doublecheck and make sure it is not actually coming from your system.
The Upshot
To a layman, these all might as well be viruses. But if you want to fix them, you should not assume your antivirus program is the solution, or tell someone helping you with technical assistance that a virus is the problem. Chances are you really don’t know if it’s a virus or at all, and chances are that it isn’t. There are many, many reasons a computer may not be working properly, i.e. running slowly or freezing. These are usually hardware problems or problems caused by software you installed on your system. It could be not enough memory. It could be running too many programs at once, even ones you don’t realize are running in the background. And yes, some of your cute little programs you downloaded, such as weather bug or various browser toolbars often have spyware built into them. That is why you should never download a program unless you know and trust where it is coming from, and even then some common brand-name companies bundle such things in their common products, and it is up to you to read the fine print.
So the next time something unexpected or unwanted happens to your system, don’t blame it on the bogeyman. Simply explain the symptoms of your problem to the person who will help you fix it. Of course, running your antivirus and anti-spyware programs won’t hurt, but even these don’t always catch the culprit. Not making assumptions is the most important thing when dealing with this sort of problem. And whatever you do, don’t keep adding more software, or restoring over and over again, to fix the problem. You can never catch the bogeyman, until you know who he is.
You keep send me email, but all I read is blah-blah-blah.
That’s right, I’m talking to you.
This is a note to apologize for not “passing on” or “sending back” your lovely animated, huge-lettered poems with midi music, or free offers for computers and trips to Disney or a cure for some non-existent little girl’s illness if your email gets sent to millions of other people, who also apparently do not realize there’s no such thing as an “email tracking system”.
If you don’t get them back and no one gets them forwarded from me, I assure you it doesn’t mean you’re not my friend, I hate America, or don’t love Jesus. I just don’t beleive in using email for the sake of itself, i.e. chain mail fueled by the imposition of bad luck or guilt.
I forgive you, if you forgive me, but think of it this way. If you had to put a 29cent stamp on every email you sent to each person (plus and extra $2 for every blaring midi music nightmare that springs upon friend and foe alike without warning), would you send it? Would you take the time to call the 144 people in your address book about it, realizing afterward you haven’t spoken to half of them for over a year? Is the best thing you can say to them after missing their last five birthdays “reply back and pass this poorly constructed sonnet about teddy bears on to 10 people or you don’t care about me”?
Would they really want to cry over Santa visiting a veteran on Christmas Eve more than the joy (and surprise) of YOU actually visiting THEM?
Yes, that’s what forgotten relatives, long-lost friends, and your insurance agent and lawyer really want out of life – finding in their inbox jokes about how cold it is in Buffalo, reprints of misinformed urban-legend editorialists, and poems about God and angels, smiles and hugs, and just plain weird recycled commentaries on things like “In God we Trust” and 9-11. And they REALLY love opening an email attachment within an email attachment times ten just to reassure themselves that you sent it to them for a good reason. It’s like opening a huge box containing a box and so forth until you’re left with a ring-sized box, only to find a turd in it.
Remember, only you can prevent forest fires and chain letters.
If you like the people in your address book that much, maybe you should send them a fruit basket or something. (Guilt of the plank in my own eye ensues.) I dunno – maybe you should CALL THEM. But mass email is the ultimate excuse to not feel guilty for not staying in touch. But I’m sure an email that has nothing to do with you or them addressed to 100 people does the trick, right? And one million more email copies of “Footsteps” with Michael Row the Boat Ashore thumping and clicking in the background wont hurt anybody, right?
But without this wondrous medium what would you do? You would have to carry copies of chain letters and cartoons on floppy disk around so you could share the wealth of your everyday existence, because obviously more happens at the keyboard than your living room or front door.
It’s funny beacuse it’s true.
It’s sad because it’s true.
{Reprint from LiveJournal entry December 6th, 2004}
Browser Wars – Bill Gates, Sir Jim, and You
IE-Haters Anonymous
Finally, there is help — and hope — for you.
Heeding this article may not keep you in good standing with the IT community, but the rest of the world — and your checkbook — will thank you for it. The first part is a 5-step program to letting go of what’s been holding you back. The goal is to shift your perspective from emotional to realistic and from a programming-engineering mentality to that of a business person in the real world.
But first, I am reminded of what may be no more than an urban legend, but makes the point nonetheless. Engineers at NASA supposedly spent millions of dollars developing an ink pen that could write in zero gravity, as ink pens are gravity-fed. Like so many other things, they engineered it and over-engineered it, making sure it met every possible specification for every possible use. The Russians used a pencil.
I’m able to share all this with you because I’m a business person with IT knowledge, not the other way around. And a business person is worth his salt only in how well they accurately perceive and deal with market reality. Being an uber-geek or the Alpha male in the IT department is the top of the wrong ladder when it comes to this. You are a skilled craftsman — an engineer. But the success of your product is only in small part determined by the prowess of your craft, and certainly not by doing what is “best” from a purely technical standpoint. It is determined by its usability, and in particular ACCEPTANCE by the users in the real world target audience.
Remember, Bill Gates is the richest man in the world, because of business sense, not programming skill. But I’m going too far, too fast. Let’s start with baby steps.
I. Give up your idealistic crusading — you are not a general in the browser wars.
This is not some ancestral wrong to be righted, as if Bill Gates stole someone’s sacred penguin in a former life and now his corporate heirs are living off its golden eggs. There is no open source holy land to win back. No one cares if someone bought up Boardwalk and Park Place before Netscape had the chance. Since when did brand names get dragged into socio-political debates, anyway? Who cares by what means of voodoo and buccaneering Bill dominated the market. While we are busy hating the capitalist rich and praising the … well … not-so-rich-just-yet other players, the marketplace whooshes past us. They don’t lose sleep over it — they’re too busy playing the game. We need to get our own game on.
But if it helps, think of Microsoft as the new Roman Empire. They were hated by most of the then-known world (regardless of the fact it brought peace and accessibility of things like plumbing and eduction to all, whether they liked it or not). They were bullies; they were saviors. There will always be a king of the hill to be despised and knocked down, whether it be Redmond on Wall Street or America in the United Nations. Straighten your tie, leave the water cooler tribe, and get over it. Why? Next point, if you please.
II. Realize you do not own a browser company
Once you get off the high horse of step 1 — and only then — will you be ready for this step. In the battle of the browsers, who wins the browser wars is NOT your concern. Market reality is, but we’ll get back to that in a later point.
Unless you own stock in it or work for MS, AOL, et alia, you have no reason to push brands on other people with taglines and “best viewed with” whore-links. The few people who care already made up their minds. People who don’t, such as your CUSTOMERS, think it’s geekish and pointless at best, annoying and unprofessional at worst. No one is switching browsers because they see “Take Back the Web” on a bunch of random web pages, except the politically fickle. But the point is … repeat after me: IT IS NOT MY CONCERN. My concern is to deal with market reality, not be the ant who tries to push the SUV of the web to the gas station of my preference.
III. Understand that standards are not always standards
Are your sites W3C compliant? Congratulations — you win a pocket protector. And if you sell it on eBay, you might get a few pennies more than you would from a rusty slide rule. That’s because W3C, no matter how well thought out in theory, is just an artificial, arbitrary standard. Yes, the IDEA of standards are really useful. But they are only helpful in the real world when they are ESTABLISHED in the real world, as in the case of say, metric (IS) weights and measures. At some point, they became “the” standard and not just “a” standard (a proposed standard).
But it seems some of you need the news flash again. W3C is not THE standard. A committee of armchair political techies who think they are saving the virtual world with their own IT wisdom does not establish a standard, no matter who they are and how good it may be. What is requires is wholesale compliance, starting with ALL the biggest players, which they do not have. In other words, it is more accurate to say that a significantly dominant practice, code, even brand, is the real standard, not a paper one. Right now it’s code that works in Internet Explorer.
Since all standards are established by action and not merely decree, we go back to the Romans. 2000 years ago, they did something genius. They made all their vehicles with a particular axle width (incidentally, the same width of American railroads once they became standardized). On one hand, if they didn’t do this instead of just making it a “law” (standard by agreement), it would have meant nothing. But they did.
The result? It was pointless for the leaders of other nations to “make” (declare) a standard of their own, even if some followed it, because most roads not only led to Rome, but were built by Rome. And most carts and such created grooves of the (true) standard width when using dirt roads. If your chariot axle width was your own choosing, you were likely to get stuck, and those complying to the less common “standard” would be passed by those who used the standard established by real life practice. So Rome didn’t merely decide on a standard when there wasn’t one — they actually did it, and it therefore became THE standard. But back to the present, as I think the reader is capable of seeing this as a clear analogy of the history of web standards and browsers.
So what about design considerations then? The above understanding doesn’t mean you shouldn’t ideally create design to work in other browsers. And it’s too easy in my opinion to make a site text-only friendly for the visually impaired not to. (In fact, a certain Microsoft web editing tool does most of that work automatically.) But common sense means doing two things.
Put down your cross and holy water if you haven’t already and design for Internet Explorer FISRT. If you are a web developer by profession, it may be a good idea to use that as your browser by default (O, the horror!) so you can see the web the way most people do. Use Firefox or Opera on your iMac or whatever you use for your personal machine if you have one, but seeing with the eyes of your audience goes a long way when at work. (Of course this goes the same for screen resolutions — you can always tell when someone designs page on a huge monitor and isn’t paying attention to this factor.)
The point is to NEVER ignore how IE renders your pages — like it or not, the people who use it are the lion’s share of any website’s target audience. You may as well put your best foot forward there if you can’t make a code or design work on all browsers. That would be like a French company tending a global market not having their website in English first, with French and other language options second, or worse yet not having it in English at all. To defy the market that way would be pride, not sense. So if it doesn’t work in IE and it’s necessary, drop it without hesitation or regret.
Now with your priorities finally straight, the question is how much time to spend on less-used browser compatibility? You have to decide case by case what is worth the trouble and what is not based on many factors. In the example of Rome, is your particular journey worth having an extra axle width in the trunk to more easily transfer a neighboring country’s lands? Some people today would have a cart for each one, or rather a separate page that pulls up depending on detected browser. It’s a lot of work for some low-paying projects, and not always necessary for big ones if you cross-design design and keep it simple. You have to weigh what your time is worth, and know it’s not always reasonable to expect to please everyone.
As long as essential features work and don’t look bad in the other browsers, you’ve done your job. My rule of thumb? If code or design that is very common doesn’t render on a rare browser (or similarly at a very large or small screen resolution) the viewer has these problem with everyone else’s web pages as well, so wont think ill of it.
IV. Stop making (and taking it) personal.
This step separates the men from the boys. It separates opinion from fact. What browser is best is opinion; which one is used most if fact.
Because most geeks never can make it past Step 2, doing something like defending the IE standard over W3C compliance is heresy. You will be burned at various user groups’ stakes, but not in the board room. So try to live with that. The W3C isn’t buying from your shopping cart or giving you visitors to beef up the worth of your ad space — real people are. Think of them first. Think of the children (COPPA compliance as needed, of course).
But if you defend this point to geeks, they think they are hurting your feelings when they use the term “good browsers” to your face to refer to non-IR clients. “Good” is an opinion, valid or not. “Dominant” is a statistical fact they can take up with God, the universe, and everything, if they don’t like it, but IT’S NOT YOUR BATTLE anymore. You’ve overcome your own denial. And “standard” is something business people and HTML jockeys will never agree on. But now you have the edge. Don’t rub it in their face.
Trust me — it doesn’t win friends.
So now you graduate. This last one is like the last of Buddhism’s “Ten Bulls” when the enlightened one (that’s you now, silly) goes back out into the world to shine for others.
V. Now you are ready to deal constructively with marketplace reality.
Recap what you’ve learned. It doesn’t matter what browser sucks more than another and by how much. It doesn’t matter if the richest man in the world dictates the direction of the web right now. What matters is that until you accept it — and make the best of it — you are still mentally in your parents basement fighting over why your PS-whatever is better than your best friend’s XBOX instead of doing your job.
The Roman Empire fell, as do all empires in politics and the corporate world. And if you did your homework above, it wont matter what is the dominant browser, platform, whatever. Garden of Eden or the New Babylon, following the “when in Rome” principle just makes business sense.
There. Is the monkey off your back, or should I expect hate mail?
Yahoo! Phishing
This one even uses a graphic from Google Images at the end, LOL.
![]()
Case Number: 8941624
Property: Account Security
Contact date: 19-08-2010
Iraqi Stash, but Really Nigerian
This scam is similar to what I expect f rom my Skype buddy pretending to be a brigadier general in Iraq.
Hello,
Good day and compliments, I know this letter will definitely come to you as a huge surprise, but I implore you to take the time to go through it carefully as the decision you make will go off a long way to determine my future and continued existence. Please allow me to introduce myself. I am Lt. Ken William, a US Army serving in the 3rd Infantry Division in Iraq.
I am desperately in need of assistance and I have summoned up courage to contact you, presently am in Iraq and I found your contact particulars in an address journal. I am seeking your assistance to evacuate some funds which was stashed in a Trunk Box, to the States or any safe country of your choice; as far as I can be assured that it will be safe in your care until I complete my service here. This is no stolen money and there are no dangers involved.
SOURCE OF MONEY:
Some money in various currencies was discovered and concealed in barrels with piles of weapons and ammunition at a location near one of Saddam Hussein’s old Presidential Palaces in Tikrit Iraq, during a rescue operation, view the link below for verification.
http://news.bbc.co.uk/2/hi/middle_east/2988455.stm
It was agreed by all parties present that the money be shared amongst us. Although, some were reported to be sent back.
This might appear as an illegal but I tell you what? No compensation can make up for the risks we have taken with our lives in this hell hole. I have now found a secured way of getting the package out of Iraq for you to pick up. I do not know for how long I will remain here as I have been lucky to have survived 2 suicide bomb attacks by Pure Divine intervention. This and other reasons put into consideration have prompted me to reach out for help.
If it might be of interest to you then endeavor to contact me and we would work out the necessary formalities but I pray that you are discreet about this mutually benefiting relationship.
Should you have any reason to reject this offer, please and please delete this message immediately, as any leakage of this information will be detrimental to the US soldiers here in Iraq and especially to me.
Seriously, I want you to help me.
Waiting,
Lt. Ken William
IRS Spoofing for Mal-ware
Remember, anyone can say they are sending mail from any address. Of course, the misspelling of “submission” and a lack of understanding what a W-2 doesn’t help their cause …
From: Internal Revenue Service [noreply@irs.gov]
Subject: W-2 form update
Attachments: w2form.doc (88 KB)
We would like to inform you that as of the 16th of June
you are late in updating your W-2 form submition with the new updated version. Please send us your completed W-2 update form by 01/07/2010. The updated version of the W-2 form is attached to this message.
Internal Revenue Service
And then you open it (the Word document itself is harmless):
But the object itself, actually named “Copy of p5020.exe” is the virus / mal-ware.
Why Psychology And Philosophy Are Vital To IT
{From 2004}
Just reading a recent issue of Infoworld, an article by Jon Udell caught my attention with a tagline of something like “If Google Ran Your Desktop”.
I tend to find articles all the time in IT periodicals that scream out “someone is using more than common sense here”, showing insight into real life problems. Not programming or engineering problems, mind you, but problems realted to the way humans actually need and use computers.
This particular topic was more concerned about the rational implementation of a dynamic taxonomy to describable data and the social implications both from and onto actions within a networked system.
In other words, how a large number of people categorize things (such as letters, photos, programs, whatever) is both determinable by group dynamics and determines the efficiency of the organizational system. The fact that this is all about using computer networks is almost incidental.
In fact, information technology is nothing more than a useless toy without people who understand psychology enough to make it work for a human being, sociology to make it work for large numbers of human beings, and philosophy to be able to consolidate all of these issues in a way that is both technically possible AND desirable. And if it isn’t possible, it is THIS and not the technology itself that will drive the necessary innovation.
So, YES, I AM using my Philosophy degree in what I do for a living.
😛
WiFi and Wireless Networks Simplified
{Origianlly published in the Western New York Paralegal Association newsletter, 2007-08}
All techno-jargon aside, we all know that computers, phones, printers, and other devices communicate without wires all the time in today’s offices and cities. The two main ways are Bluetooth and WiFi. They use different signals and patterns of data, just like television and radio are on different wavelength bands and read by different machines.
Bluetooth is most common for individual devices to “talk” to each other, such as a cell phone and a wireless headset, or a palm pilot and a computer, synchronizing data such as a schedule calendar or address book. It’s also used as a substitute for infrared connections, such has printers and keyboards, but does not require direct line of sight (like a TV remote). It is considered idea for simple devices sharing small amounts of information.
Most networks, however, use WiFi (associated with some “802.11” standard, the number you will see on many device boxes when you buy them). It can have a range currently of up to about 300 feet. That means two important things. First, you can network a bunch of computers together with a WiFi wireless router. Secondly, people with a laptop can go into such a zone — a “WiFi hot spot” — and access the network, which also can mean Internet access if the network is set up to share a connection to the Internet.
The good news is that being able to connect to a WiFi network is easy. All you have to do is have a computer with a wireless (WiFi) card and physically be in the hotspot (range of the signal).
There are hotspots cropping up all over the world, in cities and towns, hotel lobbies and food courts. Some are advertised more than others, and there are many web sites that list and map out publicly available hotspots. Just be aware that most places provide the connection for free, but not all. For example, access at Panera Breads currently is free, while Starbucks charges a fee (call ahead for rates). However, if the Starbucks is across the street from a hotel lobby, you may be in range and use theirs.
Some municipalities are even working toward universal connectivity by turning a downtown area, village, or even a whole county into a “hotspot” with coverage throughout. This will be much easier with new technology being developed as we speak to increase range and set up infrastructure.
But for businesses and individuals with their own wireless network, the bad news is the same as the good news — being able to connect to a WiFi network is TOO easy. If you have a network that is not secure, anyone within the router’s reception area can access any shared files, printers, or Internet connections on the network. It could mean people in the next office over — or even someone parked on the street nearby — could potentially access your network. It may or may not matter if your neighbors “borrow” your Internet connection, but any shared files, depending on the setup of the network, could potentially be copies (stolen), deleted, or changed.
To secure a network does not mean having a “firewall” to prevent attacks from the outside world, which used to mean just your Internet connection. It means giving out rights to some machines and not others, just as in a wired network. This is ordinarily done by installing an encrypted “key” — a long series of numbers and letters — on computers that are supposed to have access. A company’s technical support people should be able to handle this, or you can read the instructions that come with the purchase of a wireless card. The key is generated by the computer that controls the router, the instructions for which come with that device when you buy it. That way, when someone using a wireless-capable laptop strolls by the office or home where there is a network, it will still show up as available to access, but not be able to do so — unless they have the key.
Lastly, be aware that if you have files on your laptop that are “shared” (in a networked folder, common for personal computers since Windows XP) may be accessible to other people on a network, even a public one.
As a businessperson or professional, the important thing is that it is your responsibility to protect your data, which often includes clients’ data. Medical, legal, and financial professions in particular may be required to protect such information and may be held liable if it is stolen when it could have been protected by simple networking security. There are actually people hunting for it, scouring office buildings and neighborhoods for an unsecured network with sellable information.
The bottom line is that the world we live in is going wireless in leaps and bounds. Apart from the risks of not knowing the basics of how it works, understanding WiFi and wireless networks is a blessing too great to pass up. Soon — very soon — you will be able to access anything, at any time, from anywhere, and wireless is the way it will be done.